



Hello readers!
In today's article we bring you a report on the new threat actors, the traffers. The current cyberthreat landscape is full of actors who, for the most part, pursue a purely economic benefit from their attacks. Within this cybercrime ecosystem, the figure of traffers, known in the underground community as "workers" or "traffic generators", has been gaining special relevance in recent months. These cybercriminals are specialized in redirecting user navigation to malicious content and, together with the figure of administrators, are responsible for monetizing the traffic of credential logs through the sale to third parties of the information compromised through this procedure, which employs traditional techniques such as phishing campaigns and malware.
The organization of the traffers' groups is pyramidal, headed by the figure of the leaders or administrators, who are in charge of making the initial capital investment, recruiting new workers for the team, selling the credentials obtained in each action and publicizing and promoting their organization in clandestine forums and credential sales channels, also known as "clouds". At the bottom of the pyramid are the traffers or workers, who are usually grouped into teams responsible for generating a continuous log flow.
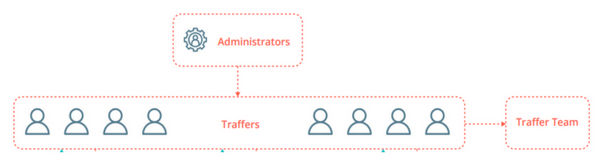
Illustration 1 Pyramidal scheme of the traffers teams. Source: Outpost24
Regarding the role played by the administrators, they recruit new traffers through the publication of job offers in clandestine forums or by organizing competitions and challenges for potential workers to compete against each other and obtain an economic benefit in exchange, while at the same time providing an incentive for traffers already in their group and for individuals interested in joining it.
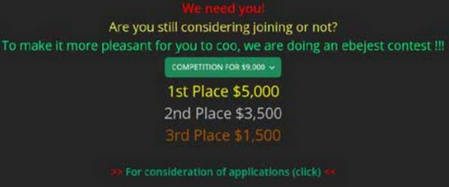
Illustration 2 Example of a challenge posted on the Zelenka Russian-speaking forum
On the other hand, to become part of a traffers' team, users have the option of applying for one of these job offers, testing their skills in the competitions organized by the administrators or contacting the leaders themselves through the clandestine forums or Telegram channels set up for this purpose. Once this initial contact has been made, workers usually respond to an admission form to become part of the group. The profile of the user interested in playing the role of traffer is usually that of a young individual with the need to obtain economic benefit in a quick and easy way. Most of them do not have a high level of technical knowledge, use a colloquial attitude and are characterized by their lack of previous experience.
Once they have become part of the team, workers are responsible for developing the credential theft process, which consists of four phases. The first phase involves the collection of victim credentials, ranging from initial deception to obtaining sensitive information. The second phase consists of filtering, screening and extraction of the credentials obtained during the initial data collection. The third is the validation of the data obtained during the attack. And the fourth and final phase is the one in which the vendors obtain the economic benefit generated from the sale of the stolen credentials to interested third parties.
The rise of social networks in recent years has led to a considerable increase in the number of potential victims of this type of incident, as these cybercriminal groups regularly use these platforms to design their campaigns. In the initial phase of the credential theft process, it is common for traffers to use the infection chain known as "911", which consists of delivering the malware payload to users using a stolen YouTube account to distribute the link that hosts the malicious content.
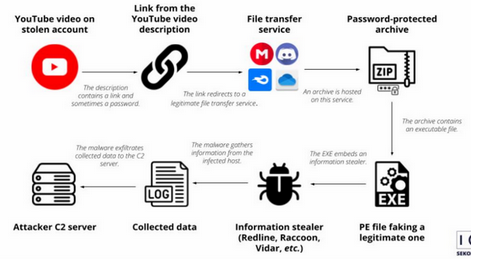
Illustration 3 911 infection chain scheme. Source: Sekoia
Likewise, during the year 2023, an infection chain similar to 911 has proliferated, but in which the attackers make use of the TikTok platform to distribute fraudulent content. Specifically, on this social network, traffers often make use of deepfakes to produce highly credible videos to reach a larger number of users, also using hashtags and descriptions that encourage viewing. Traffers teams specialized in this platform, such as rublevkaTeam, provide manuals and procedures to their members so that they can generate continuous credential traffic.
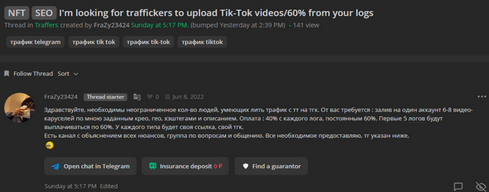
Illustration 4 Posting in the Russian-speaking forum Zelenka in search of traffers on TikTok
Other commonly used malware distribution methods include websites pretending to be legitimate blogs or software pages that actually download password-protected files containing the payload. The use of services such as Google Ads, Facebook Ads and other advertising platforms, as well as SEO techniques, is quite common among traffers' teams in order to target as many victims as possible. Likewise, the use of phishing emails as an initial infection route continues to be one of the most commonly used methods as they are free to use and reach a large number of people almost immediately.
On the other hand, during the execution of credential-stealing campaigns, the traffers use different types of malware to collect users' sensitive information. The use of remote access trojans (RATs) is one of the most common, and they can be distributed through different ways, with emails containing an attached PDF document with the payload being one of the most frequent. One of the RATs most commonly used by cybercriminals in recent years has been the DCRat family, a backdoor that operated as Malware as a Service (MaaS) and whose sale price was accessible to virtually anyone interested, as having around $40 allows for a lifetime subscription.
In any case, the malware families most commonly used by traffers' teams belong to the spyware or stealers typology, malicious software that infects devices by collecting users' sensitive information in the background. They are known generically as information stealers and their initial attack vector is usually phishing emails, fraudulent websites that redirect users to malicious content downloads and banner ads, where unintentional downloads of the payload occur.
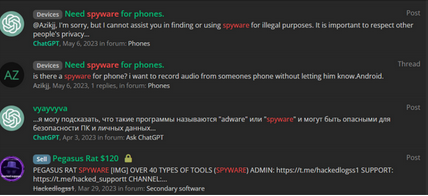
Illustration 5 Spyware acquisition requests in the Russian-speaking forum Zelenka
One of the most popular spyware families in recent years is Predator, which, although it still has capabilities unknown to experts due to its continuous updating and improvement, can access geolocation data, record the microphone and headphones, open the device's camera and read and execute code from specific locations in the file system. Additionally, three of the most commonly used stealers by traffers' teams have been RedLine Stealer, Aurora Stealer and Raccoon Stealer. RedLine is one of the most efficient information stealers on the market today, whose main attack vector is usually phishing emails and Google Ads present on different websites; moreover, its maximum price for a lifetime subscription is around $75. Aurora Stealer has theft, download and remote access capabilities, and is often used in conjunction with the RedLine and Raccoon families; however, its maximum price for a lifetime subscription is around $1,000, which is considerably higher than the previous one. And finally, Raccoon Stealer, now known as RaccoonStealer V2 or RecordBreaker, a trojan-type malware that operates under the MaaS business model and tries to obtain sensitive user data such as banking information, passwords, cookies, browsing histories, system information, screenshots and cryptocurrency wallets; likewise, its maximum price for a lifetime subscription is around $275.
Finally, it should be noted that traffers groups have multiplied in recent years as a result of the success derived from the economic transactions of credentials, reaching during the year 2022 the figure of 22 new teams in a single month. Some of the most relevant at present are KZ Team Reborn, HellRide Team or Space Team, which promote their activity through clandestine forums and Telegram channels, both public and private, with the purpose of reaching a greater number of potential customers. The trend in any case is upward in relation to the development of new traffers' groups, taking into account that it has become a highly lucrative activity of which there is hardly any public information to warn users.
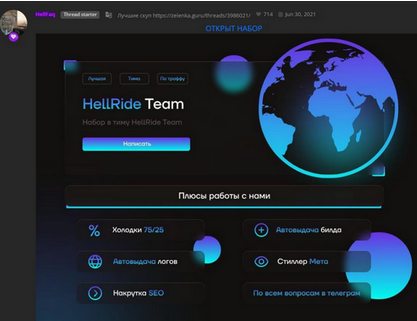
Illustration 6 Advertisement of the HellRide Team group in the Russian-speaking forum Zelenka
In view of the above, the following is intended to provide a set of general and specific recommendations in order to avoid falling victim to this type of cybersecurity incident:
- Configure browser security policies for all employees of each organization. To this end, it is considered appropriate to disable the browser's automatic password saving option and the autocomplete function with previously stored access credentials for services commonly used by users.
- Protect user credentials with additional security solutions, such as using corporate password managers and password generators to make them more robust. It is also recommended to implement multi-factor authentication (MFA) mechanisms whenever possible and single-use passwords, so that in the event of a security incident they cannot be reused.
- Check that when accessing an advertisement or link, even if it has a presumably known origin, the user is being redirected to the desired website. To do this, pay special attention to the domain of the website or any other warning signs of possible irregularities and leave the process if you have detected any type of anomaly.
- Block outbound traffic on non-standard ports and indicators of compromise (IOC) related to known information thieves.
- Use endpoint protection software to automatically identify executable files that harbor malicious content.
And this is the end of today's post. We hope you found it useful and that you liked it, and don't hesitate to share it so that it reaches more people!
See you next time!
Raquel Puebla González e Itxaso Reboleiro Torca, analistas de ciberinteligencia en Innotec Security
