



Hey everyone!
Taking into account that ransomware is one of the types of cyberthreats with the greatest global impact at present, Entelgy Innotec Security has studied the families with the highest incidence during the second half of 2022, the geographical areas and business sectors that have been most targeted and the most relevant events in relation to the predominant families, as well as examining the geopolitical and geostrategic impact of this type of operations within Spain, all with the purpose of knowing the current trends and, in turn, discerning which events or situations are most likely to occur in the future.
Regarding the preeminence of ransomware in the global cyberthreat landscape, it should be noted that up to 1065 successful ransomware cyberattacks associated with 31 different families have been identified during the second half of 2022 alone, with LockBit, BlackCat (also known as ALPHV) and Hive leading the way, which between them accounted for around 50% of the total incidents. In addition to the above families, Royal and BianLian have also been notable, which, with a short period of activity, as they were identified in January and August 2022 respectively, would have been completely disruptive by breaking the access barrier to the TOP 10 ransomware cyberthreats of the second half of 2022 in just a few months since their emergence.
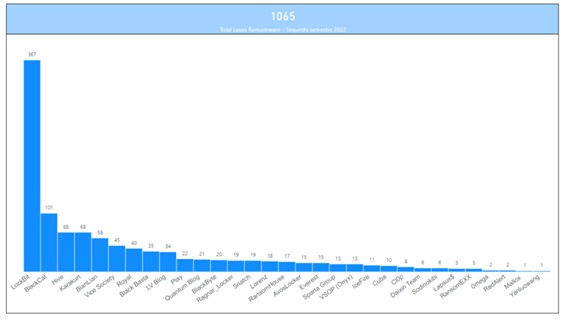
Illustration 1 Affectation by ransomware families (second half of 2022)
Overall, it was found that the peaks of ransomware activity occurred in July, when the total number of threat actors increased following the dissolution of Conti in the first half of the year, and December, when a large number of actors and cybercriminal groups take advantage of the absence of some incident response team employees due to the last holiday period of the year to carry out cybercriminal operations with a higher probability of success. Similarly, there is a lower level of activity by ransomware actors in August, suggesting that this class of organizations has a high degree of professionalization similar or comparable to that intrinsic to legitimate entities, with similar activity schedules and workloads.
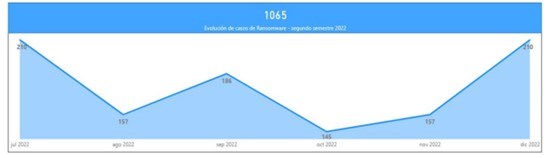
Illustration 2 Ransomware activity by month (second half 2022)
In addition, it has been found that most of the cyberattacks have affected the United States, Europe, the Arabian Peninsula, Central America, Indonesia and Canada, which allows us to consider that ransomware actors, mostly aligned with the interests of the Kremlin, advocate directing their operations against priority adversaries such as the United States, whose hostilities are currently manifest and considerable, resulting in it alone receiving more than 40% of total ransomware operations, and the European countries that have openly supported Ukraine after the beginning of the war conflict. Indistinctly, although to a lesser extent, there has also been a predilection for digitizing targets, as they provide threat actors with a higher probability of success and, with it, certain guarantees of monetization.
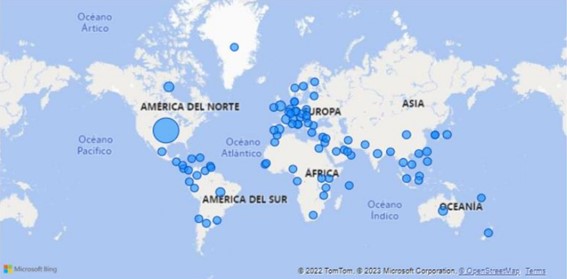
Illustration 3 Global ransomware incident impact map (second half 2022)
Another remarkable aspect refers to the impact by sector experienced in the second half of 2022 in relation to ransomware incidents, which have managed to impact up to 50 different work sectors. Among them, manufacturing, IT, retail, education, healthcare, construction and banking have been particularly affected. Consequently, those services that directly influence social, cultural and economic welfare are of particular relevance, a fact that would most likely result from the escalation of the current European war.
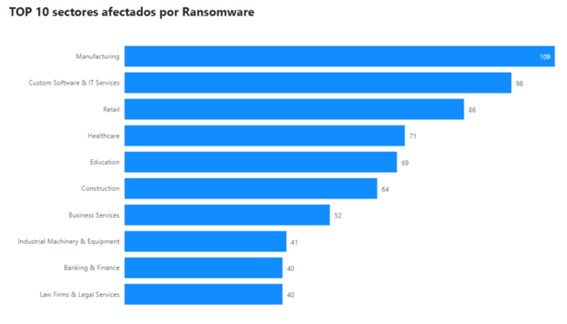
Illustration 4 TOP 10 impact by sector (second half 2022)
Within Spain, there have been 35 successful ransomware cyberattacks on Spanish organizations, which in more than half of the cases would have been executed by the threat actor Sparta Group, a subdivision of the pro-Russian hacktivist group Killnet that emerged in February 2022 as a result of the Russian invasion of Ukraine. In this case, Sparta Group's intention to act against Spanish entities with a high probability would have responded to geopolitical motivations, since the beginning of the cyberattacks coincided temporally with Spain's decision to expel all Russian ambassadors from the nation and KillNet's subsequent announcement declaring cyberwar against the United States and several European countries, among which Spain is in fact included. However, Spain did not appear to be the predominant target of the cybercriminals, as KillNet reportedly made public that the actions against the country would be considered a training method for its members, the purpose of which would be to gain practical experience to direct their operations against targets of greater interest to the collective in the future.
Other ransomware threat actors that have directed part of their operations against Spanish entities have been LockBit, Vice Society, Hive, LV, AvosLocker, RansomEXX, RedAlert and Snatch, although in insignificant proportions if compared to the number of total incidents for each of them.
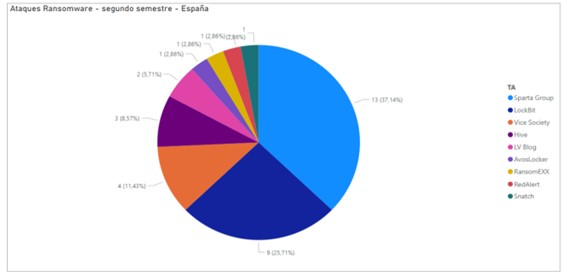
Illustration 5 Affectation by actors Spain (second half 2022)
In addition, within the national sphere, ransomware actors have managed to affect 17 different work sectors, although these do not differ greatly from the sectors impacted at the global level. In general, in this case, cyber-attacks are directed against work sectors that are not very digitized and have little experience in fighting cyber-threats, thus giving in to extortion becomes a likely option in these cases. Therefore, their main motivation during the second half of the year has been predominantly economic and not geopolitical, since the operations have not targeted high-impact organizations or those that could lead to a decisive destabilization of the socioeconomic and cultural landscape, which is in line with LockBit's behavior and with the alleged tests carried out by Sparta Group, although in the latter case the choice of Spain as a target country could have initially responded to the decisions taken by the state in relation to the current European armed conflict.
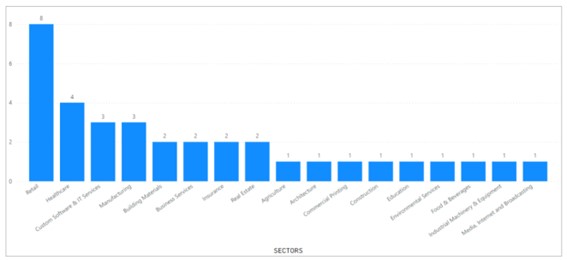
Illustration 6 Impact by sector Spain (second half of 2022)
In any case, everything seems to indicate that those ransomware families that are achieving more success are those that advocate advanced monetization techniques such as Ransomware as a Service (RaaS) and double and triple extortion, which does not seem to be tending to decrease in the short term, but rather the opposite. In this sense, it is more likely to consider that the major ransomware actors will be advocating the incorporation of new monetization techniques that can increase the effectiveness of the extortion they carry out, while the minority actors will try to adopt the already known models. In fact, actors such as BlackCat have started to use quadruple extortion techniques, adding to the already known techniques a phase of extortion of customers, employees and business partners during which the threat actor would make them aware of an incident affecting them, with the purpose that they themselves demand that the compromised corporation agrees to pay the ransom demanded by the cybercriminals.
Moreover, while Hive appears to have been dismantled as part of a joint law enforcement operation between the US and German authorities, LockBit expresses high levels of resilience that allow it to continue to maintain a hegemonic position in the ransomware cyber threat landscape, with levels of activity and success similar to those of the first half of 2022 despite having endured in the second half of the year relevant leaks concerning the builder that uses its encryptor and the arrest of alleged members of the group, as in fact occurred with Mikhail Vasiliev during the month of November in Canada.
As Hive is the only one of the three major ransomware families to have expressed a predisposition to target critical infrastructures in different countries (logistics, transportation, food, education, health, energy and government) and considering that the most recent information refers to the fact that it has been dismantled, it is very likely that in the next six months monetization will continue to be the main motivation behind the activity of the major ransomware actors, although the choice of targets will continue to be aligned with the interests of the Kremlin, which means that the major targets of these actors will continue to come from the US and European environment in the future.
So much for ransomware trends in the second half of 2022! Did you expect so many, or were you surprised? In any case, if you liked it, don't hesitate to share it on your social networks or with your trusted people! We’re sure that it will be useful for many people ;)
As always we say: see you in the next post!
