



Hello, readers!
We have all heard about the famous LockBit ransomware actor, but what do we really know about it? When did it emerge? What is its intentionality? In today's post we bring you these answers, going deeper into the analysis of this notorious actor. Let's get started!
LockBit has become the predominant family in the ransomware cyberthreat landscape practically since its emergence in September 2019, when the first traces of activity linked to it were identified. Since then, and with no signs of any change in this regard, it has established itself as the most active ransomware cyber threat with the highest global impact on a wide variety of organizations and institutions.
This ransomware family, which until the development of version 2.0 was prematurely referred to as "ABCD" because its developers incorporated this name as an extension to the compromised files during encryption, was developed by threat actor Bitwise Spider, a Russian-speaking cybercriminal group possibly aligned with the Russian government, as it promotes its activity through underground forums that make use of this language and prevents operations both by itself and its affiliates against post-Soviet states.
An intrinsic characteristic of this threat actor is its constant incorporation and experimentation with the latest cybercrime trends, a fact that consolidates it as the predominant cyberthreat and prevents other cybercriminals from disrupting its hegemonic position in this scenario. In fact, as with other ransomware families, it uses Ransomware as a Service (RaaS) techniques, whose statistics show that it has the highest levels of membership to date; and double extortion, as it threatens to leak sensitive information after the compromise of a given system. It has even been found that it has recently experimented with the incorporation of triple extortion tactics, adding to the previous risk the possibility of causing unavailability of the services affected by the ransomware through a denial of service (DDoS) campaign, which would increase the damage to the affected organization and, as a result, could make it reconsider its decision about whether or not to pay the ransom demanded by the cybercriminals.
With the development of LockBit ransomware version 2.0, which took place in June 2021, Bitwise Spider was consolidated as the biggest cyber threat in this scenario, whose peak is still in force today. This situation took place thanks to the incorporation of advanced functionalities such as StealBit, which substantially increased its information extraction capacity; improvements in self-propagation mechanisms, shadow copy elimination capabilities or evasion of User Account Control (UAC) mechanisms for privilege escalation, among others. Specific versions were even developed for Linux, in addition to modifying the extension that was added to the encrypted files to the one that has been maintained to date, "[.] lockbit".

Illustration 1 LockBit 2.0 Blog Logo
In 2022, LockBit was once again a real disruption in the global ransomware landscape with the release of version 3.0. This event took place shortly after the FBI and Microsoft respectively disclosed several indicators of compromise and certain bugs that allowed the encryption process to be reversed, developments that were widely discussed in various underground forums and finally acknowledged by LockBitSupp, the official profile of this threat actor on the Deep Web, who at the same time confirmed that they were finalizing the development of LockBit 3.0.
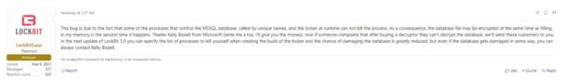
Illustration 2 Response from LockBitSupp confirming version 3.0. Source: https://socradar.io/lockbit-3- another-upgrade-to-worlds-most-active-ransomware/
In the same time period and in parallel to the previous events, LockBit completely disassociated itself from the war between Ukraine and Russia and stated in a separate statement that they were only operating for economic and business maintenance reasons, thus disassociating themselves from the current international geopolitical and geostrategic scenario. Therefore, as with other families, their main purpose is monetization, using access vectors that combine the use of social engineering tactics, exploits and exposed RDP ports to contribute to this goal.

Illustration 3 LockBit actors' announcement declaring neutrality in the war between Ukraine and Russia
Finally, LockBit version 3.0 did not arrive until three months after the threat actor's confirmation of development, in June 2022. This version, which is still active today, incorporated major improvements, such as a Bug Bounty program whereby individuals who reported vulnerabilities that undermined their operations or identified the group's top leader were offered a certain reward. In this way, they encouraged other cybercriminals to contribute to their activity instead of competing to weaken it.

Illustration 4 Bug Bounty program in LockBit 3.0
In addition, they added an option list on their website regarding the organizations attacked, whereby sensitive information could be downloaded for a certain or indefinite period of time and the published data could be destroyed in exchange for a payment set by the cybercriminals. The Zcash cryptocurrency was also added as a payment method to those previously available (Bitcoin and Monero).
Lockbit 3.0 is also characterized by the maintenance of strict conduct and ethics codes, with clear guidelines and reluctance to carry out operations against critical infrastructures with actions that cause unavailability of services, for example, in health services whose paralysis could result in damage to health. In fact, on January 3rd, 2023 LockBit was severely criticized socially and in the media after a cyber-attack on a Canadian hospital that had caused unavailability of health services became known, with the result that, after these facts became known and it was found that one of its affiliates had not respected the group's rules, Bitwise Spider formally apologized and provided a free decryptor to the hospital. In addition, as noted above, they also do not allow cyber-attacks on entities located in countries of the ex-Soviet Union and especially advocate directing cyber-attacks against law enforcement agencies of any state that tries to undermine their activity.

Illustration 5 LockBit 3.0 Ransomware Affiliate Program Rules
They also establish on their website a set of rules that must be respected by those cybercriminals who wish to join their affiliate program, such as paying an advance payment of 1 Bitcoin, or involving the study of the reputation of the potential affiliate to their RaaS service. In this way, they try to ensure the continuity of the group by preventing potential security researchers from pretending to be potential affiliates to their service and in practice contributing to their detriment by analyzing their Tactics, Techniques and Procedures (TTP).

Illustration 6 LockBit 3.0 Ransomware Affiliate Program Rules
Another of the key aspects to highlight in relation to the LockBit ransomware actor is its high resilience capacity to resolve in a satisfactory way for the group different actions that have taken place with the intention of undermining its operations. In this regard, at the end of 2022, two events of interest occurred that resulted in a momentary decrease in the number of operations carried out by LockBit and that in the month of December were fully restored, as shown in the following illustration.
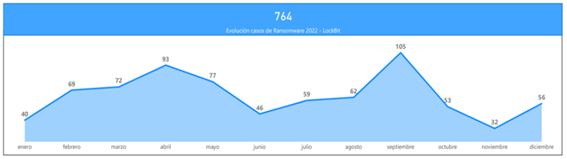
Illustration 7 LockBit 3.0 ransomware actor activity by month (year 2022)
The first of these took place in September and involved the leak of the builder of the latest version of the encryptor used by this ransomware actor by a Twitter user named @ali_qushji, which eventually led to a much more widespread diffusion through different places in cyberspace.
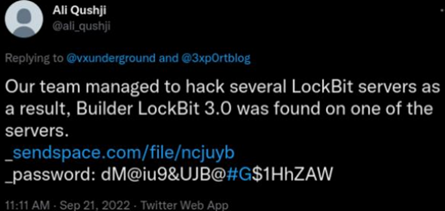
Illustration 8 Twitter post by user "@ali_qushji" disclosing the LockBit 3.0 builder
The leak allowed customizing the encryptor to modify the ransom note, as well as changing or stopping running processes and services and modifying the command and control server, among other things. Overall, the builder leak would allow any cybercriminal actor to design their own ransomware operation easily, with indispensable elements such as encryptor and decryptor at their disposal. In fact, traces of activity have already been observed from other threat actors using this builder to enter the global ransomware scene, as in fact happened with the Bl00Dy family. However, at no time did the threat actor make any reference to a possible new version to alleviate the situation, and there was no exacerbated impact within the group that would have deteriorated its activity.
What has been discerned and confirmed thanks to the analysis of the leaked builder is that, as indicated at the beginning of the investigation, LockBit continuously tries to incorporate new features and trends in vogue to increase its operational capacity. In this sense, certain similarities were observed between this ransomware actor and BlackMatter, a fact that could evidence certain connections between them that, in turn, would further increase the complexity of the cybercriminal network surrounding Bitwise Spider. Among other things, similar anti-debugging features or sending ransom notes to network printers were observed, as well as evidence of an attempt to incorporate worm characteristics into LockBit's payload, allowing self-propagation activities and lateral movements in the targeted networks.
The second notable event with an impact on LockBit's operations occurred on November 10th, 2022, when Mikhail Valisiev, a Russian citizen, was arrested in Canada and formally charged in federal court in Newark for participating in ransomware operations within LockBit and for conspiracy to damage computing devices and transmit ransom demands. Although the investigation has only just begun, one fact is clear: if convicted, he will become the first LockBit member to be formally and criminally convicted of activities related to this ransomware family, which would undoubtedly be a major blow to the group.
Despite the above, LockBit has affected 51 different work sectors internationally and 13 nationally in 2022 alone, highlighting in both cases those sectors composed mainly of medium-sized organizations that are not fully digitized, such as manufacturing, construction and retail, among others, and which, in general, coincide with the generic trajectory of most ransomware actors.
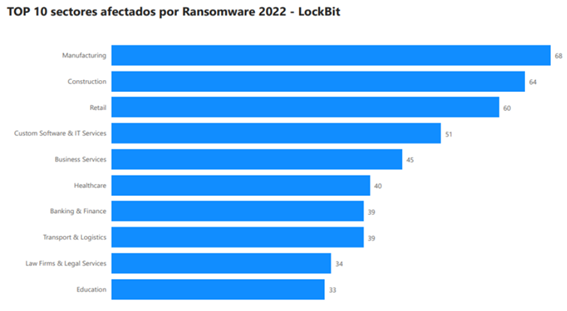
Illustration 9 TOP 10 sectors affected by Ransomware 2022 - LockBit
However, the number of cyberattacks perpetrated against Spanish organizations is not significant, and does not allow us to consider that the group or its affiliates focus their campaigns against the nation, since only 2.75% of all LockBit cyberattacks in 2022, or in other words, only 21 out of 764 cyberattacks, have been directed against them.
At the national level, LockBit has mainly targeted retail, with successful cyberattacks on Cofrap Española, related to the purchase and sale of stationery, writing, drawing and fine arts items; Frigoríficos Bandeira, dedicated to the sale of meat products; the family business group G.E.T., specialized in currency exchange, real estate and renewable energies, or pharmaceutical entities and distributors such as Cirici and Fedefarma. It has also directed its operations against private educational organizations, such as Elías Querejeta Zine Eskola school, dedicated to the training of filmmakers; or organizations that offer diverse business services, such as the IZO group, related to consulting, and Antea Emu S.L., linked to the prevention of occupational hazards.
A small part of the operations within the Spanish context have also been directed against organizations that provide certain essential services, such as the private hospital San José, located in Las Palmas de Gran Canaria; or Fruca Marketing, in the food sector, although at all times the operations were carried out in accordance with the requirements established by the group in relation to the availability of essential services.
In any case, given the above information, LockBit ransomware actor and its affiliates do not seem to be motivated by geopolitical and geostrategic reasons when directing its cyber operations against Spanish entities, taking into account that the number of campaigns identified is tiny compared to the total number of total ransomware incidents attributed to this threat actor and, moreover, once it has been established that it has not directed any of its campaigns within the national sphere against organizations whose compromise could undermine or destabilize the whole of society and the functioning of institutions and services essential to the nation.
On the other hand, it should also be noted that LockBit is the ransomware family that has achieved the greatest impact and breadth at a geographical level in 2022, having impacted 78 different countries, with a special focus on the United States, Russia's main adversary; most European countries and regions of Central and South America, Indonesia and Africa, the latters agreeing with the aforementioned premise related to the predisposition of this threat actor to target regions or targets not widely digitized, as well as Russia's main rivals and adversaries, which allows us to verify the animosity against Western societies and the alleged alignment of Bitwise Spider with the government even though it has publicly disassociated itself from national geopolitics and geostrategy. However, taking into account that the objectives targeted by this threat actor do not differ greatly from the national-level organizations outlined above, it can be stated that the main motivation of this cybercriminal group is monetization, keeping a low profile in relation to the targeted organizations to avoid the forcefulness of joint international law enforcement actions that could be directed against it in the event of large-scale activities.

Illustration 10 LockBit affectation map (2022)
So much for the article on the analysis of the LockBit ransomware actor! We hope we have resolved those initial doubts and that it has been useful for all of you.
Don't hesitate to share it so that it can be useful to more people.
See you soon! :)
