



Hi, readers!!
On the occasion of the publication of the technical report recently published by the company on a new investigation in which our professionals have analysed all the information available on the Conti ransomware actor, today we bring you a new publication that delves deeper into the analysis of this actor.
Conti has emerged as one of the predominant families in the ransomware cyber threat landscape since its emergence in December 2019, when the first traces of activity linked to it were identified. However, the plenitude of this ransomware would conclude in mid-2022, following unwise decisions for the threat actor that would have developed it.
This ransomware family has over time employed tactics related to the Ransomware as a Service (RaaS) cybercriminal model, which establishes a form of affiliation to a Conti usage service set up by the threat actors developing it and generally blurs the attribution of cyberattacks and increases the degree of complexity of the cybercriminal network surrounding the cyberthreat; and double extortion, whereby the threat actor carrying out the cyberattack subsequently threatens to leak the information gathered to cause the affected organization to ultimately choose to make the ransom payment demanded. Therefore, its main purpose is monetization, as the actions performed are done to increase the financial gains of the ransomware actor. To achieve this, during the infection process Conti made use of different access vectors that included social engineering techniques, such as phishing campaigns and links to fraudulent websites; exploits that leveraged various known vulnerabilities and exposed Remote Desktop Protocol (RDP) services.
Although the RaaS affiliation model attributed to Conti prevents a correct identification of all the cybercriminal groups that could have used this ransomware in cyberattack campaigns, there is a clear link between this ransomware family and the pro-Russian threat actor Wizard Spider, whose activity dates back to 2016. This threat actor, which specializes in the development and execution of Advanced Persistent Threats (APTs), is itself responsible for the TrickBot and Emotet Trojans, as well as the Ryuk ransomware, which, used together, caused international devastation for several years. With regard to the latter, it has been considered that Conti could have developed as a successor to Ryuk, as it shares some of its code with it, due to the decrease in effectiveness that the latter would have experienced following the analyses and investigations underlying the number of campaigns in which this cyber threat would have been involved.
In relation to Wizard Spider and Conti therefore, it has been estimated that this threat actor would have been composed of around 80 to 100 active members divided into different cross-functional attack teams. These teams would aggregate programmers, pentesters, open source intelligence (OSINT) specialists, system administrators, reverse engineering experts, blockchain specialists, as well as human resources staff and trainers in charge of hiring, recruiting and training new members, among others. All of them would be subordinated to a figure who would be at the head of the entire organization, according to the following illustration.
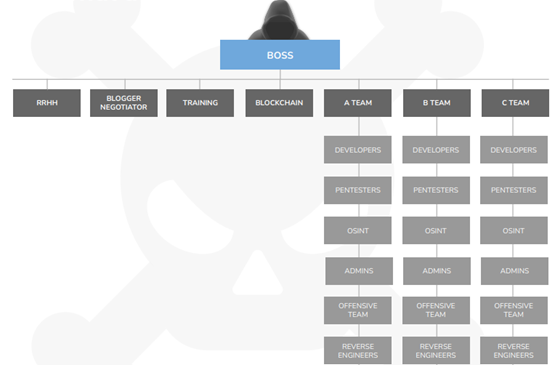
Illustration 1 Conti ransomware actor organization structure
With a solid structure containing high levels of specialization and hierarchy, and with a well-established membership model, one wonders what the inexorable decline of this ransomware actor may have been due to. Unlike other major groups, such as LockBit, Conti positioned itself openly and favorably alongside Russia after the announcement of the self-styled special military operation that this nation carried out over Ukraine in February 2022 and which has led to the European war that is still ongoing in 2023. Thus, on February the 27th, 2022 Conti launched through its official website an announcement in which it indicated that, despite claiming not to be aligned with any government, it condemned the ongoing war and, therefore, would direct its operations against any government that acted against the Russian-speaking civilian population in any region of the world, basing this course of action on what this threat actor called "Western warmongering", since it considered that the United States had been spreading threats against the entire Russian citizenry and against its critical infrastructures.
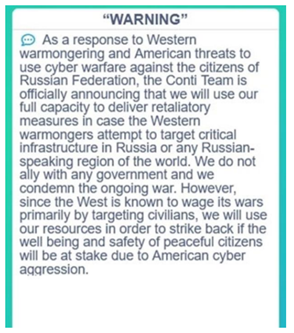
Illustration 2 Conti's statement in favor of Russia and against alleged aggressions from the West
That same day, a Twitter profile, @ContiLeaks, was created with the single intention of undermining the group's activities, leaking years of internal group conversations, documentation and details of the wallets with which ransom payments were made, and even the source code for version 3.0 of the ransomware payload. The leak led to the inevitable detriment of Conti's operations, as it provided the authorities with invaluable information about its internal workings and made it possible to estimate the financial gains made over time by this ransomware actor at $180 million. In fact, parts of the leak that took place between February and March 2022 are still being distributed today, as on January 30th of 2023 it was again identified that the ransomware code was being leaked through Telegram, allowing the design of executables that allowed file encryption and decryption among a number of other actions.
Illustration 3 Twitter profile @ContiLeaks
Illustration 4 Conti ransomware source code leaked on Telegram
For its part, @ContiLeaks claimed in an interview to be an independent Ukrainian researcher trying to undermine Conti's activity, although it was previously considered that the leak may have been due to an internal dispute within the group about public support for Russia. At the end of March, this profile ceased to be active, however, Conti has not been able to recover from the impact of the leak at any point, which has also led to its dissolution.
In fact, since May 2022, no operations related to Conti or Wizard Spider have been identified, although it has been considered that rather than a complete cessation of their operations, what has taken place is a process of splitting into new, lesser-known ransomware actors, such as Karakurt, BlackByte, BlackBasta and Quantum, which will undoubtedly require attention in the future.
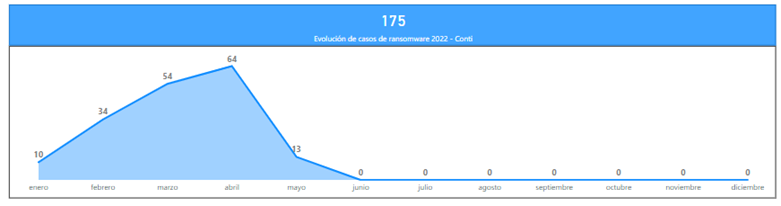
In the case of Conti, with 175 successful operations in 2022 alone and having established itself as the third largest ransomware family in the same period, it showed, prior to its dissolution, a predisposition to act against organizations from manufacturing, telecommunications and information technology (IT), construction, a variety of business services and retail, among others. This is consistent with the ransomware actors' general operations, which usually target medium-sized organizations that are not fully digitized, with the exception of the IT sector. However, in the case of Conti, and continuing Ryuk's trend, which in 2021 achieved wide coverage of high-impact public organizations such as the State Public Employment Service (SEPE), it has also directed part of its campaigns against entities in the defense and government sector, social services, healthcare and other public critical infrastructures.
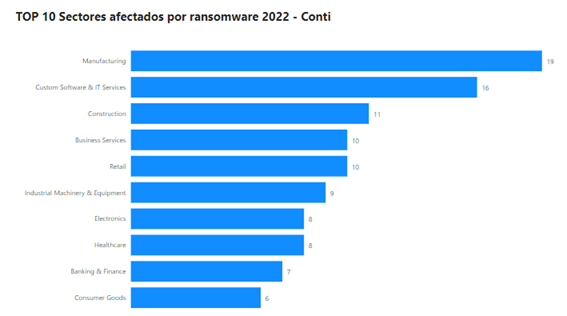
Illustration 6 Conti ransomware actor's impact by sector (year 2022)
Within the national scope, the previous trend would have been maintained in relation to cyberattacks against Spanish organizations, with special incidence of operations directed against construction, entities from the legal and juridical fields and organizations related to the manufacture of industrial and conduction materials. At the same time, Conti would have affected high-impact organizations and critical infrastructures such as Aigües de Terrassa, a local public organization in the city of Terrasa, which is directly responsible for water management in the region and which would have been heavily attacked by this ransomware in August 2020. In the same line, other Conti operations would have been directed against the University of Cordoba in 2021 or in October of the same year against the pharmaceutical organization Alter, directly attacking two other essential services of any nation such as education and the development and distribution of pharmaceutical or health products and medicines.
At the international level, its alignment with Russia is evident from the fact that practically half (47%) of the cyberattacks carried out by Conti in 2022 were directed against its main adversary, the United States, and the other half of the operations of this ransomware targeting the heart of Europe, with particular impact on Germany, the United Kingdom and Italy, among others.
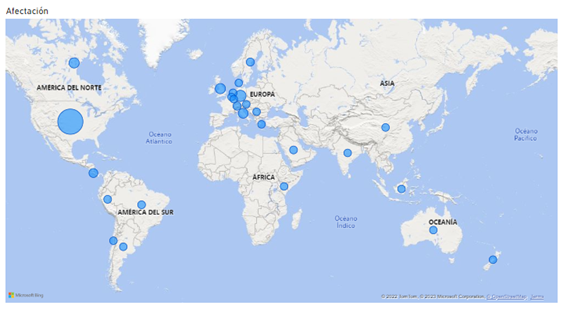
Illustration 7 Conti Affectation Map (2022)
To sum up, while it is highly likely that both Conti and Wizard Spider will not be active in cyberspace under the same name in the near future, the same cannot be said for their subsidiary groups. In this regard, there is a possibility that the ransomware actors Karakurt, BlackByte, BlackBasta and Quantum, to which the ex-Conti members have allegedly been attached and disbanded, will gradually increase their cyberattack campaigns, which in turn means that it is very likely that the targets they are trying to reach will be similar.
Within the national sphere, the growing positioning of Spain in the face of the war conflict between Ukraine and Russia in favor of the first one, added to the existing tensions in the Mediterranean between the nation and countries such as Morocco and Algeria, will presumably cause those threat actors of any kind aligned with Russia, such as the hacktivist group Killnet, to continue directing their operations against Spanish organizations and even increase their impact on the nation, thus combining the achievement of economic and geopolitical objectives. In relation to ransomware operations, it is foreseeable to consider that Conti's subsidiary actors, which will probably also show some affinity with Russia as they are composed of the same members, will continue to direct the bulk of their operations against US organizations and European countries aligned with Ukraine, including Spain. In this sense, it is possible to consider that the most targeted national organizations will be, on the one hand, those of medium size that allow the achievement of the usual economic objectives of ransomware; while, on the other hand, cyber operations will also be directed against organizations that provide essential services, such as those related to energy, water or oil resources, as well as against health and education.
And that's the end of this article about the analysis of the Conti ransomware actor! If you liked it and found it useful, we would be very grateful if you could share it ;)
See you in the next post!
