



¡Hola a todos! Hoy os traemos el artículo "Emotet: Back to the future" en inglés, un artículo de nuestra compañera Raquel Puebla González, ¡esperemos que os guste!
Dear readers, today we are going to discuss another growing cyber threat that we should be alert to and, in any case, not forget. This article is about none other than the Emotet malware.
The origins of Emotet, also known as Geodo, date back to 2014, during which time several security researchers warned of the existence of this cyber threat. From then until now, this malware, which undoubtedly evokes eras, places and faraway characters such as Ancient Egypt, as well as its deities and sovereigns, has become an almost timeless threat with a high polymorphic capacity.

In addition to the above, it should be noted that this malware has been attributed by different security researchers to the threat actor TA542, also known as Mummy Spider, ATK 104, Mealybug and Gold Crestwood, among other aliases. In relation to this cybercriminal group, it is important to note that its activity pattern is usually characterised by targeted campaigns conducted at certain times of the year, usually lasting no more than a few months of activity, and then limiting its actions or even ceasing to operate for a long period of time, ranging from three to twelve months in duration. The period of inactivity is usually used by the developers of this malware to modify the threat and promote the development of a variant that increases or improves its functionalities. In addition, TA542 was found to be distributing Emotet on underground forums during the first year it was on the move. After 2015 it became a private resource at the service of its developers, which means that this malware is now considered to be operated only by the actor TA542 or, at most, by him and a group of trusted customers that is not very large.
As can be seen in other posts on this blog, malware has evolved exponentially in recent years, which has allowed the actors that develop them to create families with very different functionalities that only a decade ago could only be rambled about. However, with the creation of new malware families and typologies being so common, it is curious to consider that Emotet has resurfaced on countless occasions eight years after its genesis. This is because Emotet is a multifaceted threat, which began as a purely economic threat and has ended up becoming a gateway for the production of highly complex and high-impact cyber-attacks.
Emotet is therefore a Remote Access Tool (RAT) that was originally conceived as banking malware, in other words, malicious software aimed at stealing credentials and banking data from the customers of financial institutions, which also incorporates a propagation capacity similar to those of malware families with worm-like functionalities. Over time, the tool has been updated, improved and even metamorphosed through the development of new versions that have implemented new functionalities. Thus, in its first versions, this code intercepted Internet traffic with the aim of stealing banking information circulating on the Internet. Unlike other malware families, Emotet logged outgoing traffic and crawled the network instead of being deployed through phishing campaigns or by attaching itself to form fields, in order to evade detection by signature-based anti-malware solutions.
Later, this malware would be updated by configuring a modular structure, making the packaging of the payload include functionalities or modules related to sending spam emails using supposed money transfers or fake invoices as a lure, stealing MS Outlook email addresses or carrying out distributed denial-of-service attacks, using botnets such as the one made up of the Nitol family, in addition to the functionalities it had already incorporated in the past related to its own installation module and the collection of banking information. In this case, the cyber threat was particularly targeted at customers of financial institutions in Germany and Austria, with Germany being the most affected country. Typically, these messages included links to external websites that delivered the payload to potential victims of the attack. In addition, the actors who developed this threat incorporated an automatic transfer system (ATS) that allowed the extraction of users' capital automatically from their bank accounts.
About a year after its emergence, following a period of complete inactivity after the malware's command and control (C&C) servers stopped sending commands to compromised devices at the end of the previous year, it reappeared with new modifications specifically designed to increase its stealth capability and evade detection, such as the ability to identify virtualisation environments where the threat could be analysed and spoof information on the attackers' servers or by incorporating an encryption methodology. Increasing its dangerousness, this malware also came to incorporate services and autostart registry keys in order to ensure its persistence on compromised systems. It also added new targets, as it expanded its activity to bank customers located in Switzerland. However, the method of spreading this cyber threat remained the same as before, sending spam emails impersonating trusted entities such as Deutsche Telekom AG and DHL International GmbH and containing links to malicious websites or specially crafted attachments, usually in .zip format and with high extension names, in order to make the executable extension (.exe) not visible to the user, which might make him suspicious.
Although in the period from 2015 to 2017 no campaigns of excessive relevance related to this cyber threat were identified, in April 2017 the spread of this malware family was reactivated with a massive campaign of sending spam emails aimed at users in the United Kingdom and which eventually affected US society. In the first case, as was traditional with Emotet, the malware was deployed by executing files, usually in .pdf format, attached to spam emails and pretending to be supposed invoices, as well as by inserting them into external links referred to in the malicious documents. In contrast, during its spread in the US it incorporated a novel delivery methodology whereby the malicious .pdf file contained a link that executed Javascript code, acting as an initial compromise vector by downloading the payload. After the malware was deployed, an error message was displayed to the user whose computer had been compromised to avoid suspicion. During the period that followed, the spam campaigns in which Emotet was distributed would increase their repertoire of lures, incorporating fake PayPal receipts, notifications of supposed shipments or bank account alerts as lures. In addition, the emails sent to spread the cyber threat pretended to come from legitimate and trustworthy entities.
In 2018, Emotet's polymorphic capacity would be observed for the first time, when it reappeared with major remodelling. It is then that it would begin to show its true destructive capacity, by being used as a downloader and/or dropper for other malware families. In other words, it acts as a first-stage payload in the compromise chain of such a cyber-attack, while other families are deployed as part of a second phase with more damaging consequences. Their success also led to campaigns involving Emotet spreading to other parts of the world, such as Turkey, South Africa and most of the Americas. Additionally, while documents with .pdf extensions incorporating links to malicious external websites or Javascript code continued to be used in the course of these campaigns, Word documents with malicious macros leading to the execution of scripts in the background using PowerShell commands also began to be designed.
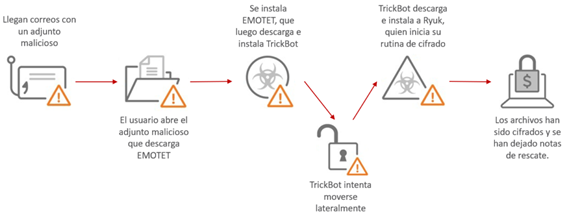
However, it would not be until 2019 when Emotet malware would put global cybersecurity in check. From then on, the most damaging campaigns attributed to it to date would take off, combining the capabilities of Emotet, as first-stage malware that acts as a downloader; Trickbot, as second-stage banking malware aimed at collecting banking credentials and data and stealing a wide range of information; and the ransomware Ryuk, as the final payload that would encrypt all the information stored on the compromised device and then demand a ransom in exchange for the decryption key. At this point a number of other techniques aimed at evading detection and building user confidence in the legitimacy of the email communication through which Emotet is usually spread would also start to be observed, such as, instead of advocating mass spam campaigns, collecting addresses from victims' address books and using previously compromised email accounts to send emails with malicious attachments to other users with whom the real conversation partner had previously initiated a legitimate conversation, all with the aim of increasing the malware's ability to spread.
Regarding the relationship between Emotet, Trickbot and Ryuk, it is worth noting that Ryuk is generally only deployed on the compromised machine once the other two families have completely paved the way, in other words, once all the credentials available on the system have been collected and access to the various network resources available has been obtained, enabling the ransomware to spread throughout the network with little effort. However, prior to the deployment of the ransomware, additional checks are performed on the compromised organisation, since Ryuk only spreads through organisational networks that would be of interest to the attackers, such as governmental institutions and entities and large private organisations. It is for this reason that Emotet, initially designed to attack individual bank customers, has migrated to targets characteristic of other sectors, such as governmental organisations and entities worldwide, with special emphasis on those located in the United States and Europe.
On the other hand, it is worth mentioning that Emotet and Trickbot are operated by different threat actors, given that the first one, as detailed at the beginning of this article, is developed and maintained by the TA542 actor, while the second one is operated by the cybercriminal group known as Wizard Spider, also known as Grim Spider, TEMP.MixMaster, Gold Blackburn and Gold Ulrick, among other aliases. In this way, each actor maintains the Emotet and Trickbot infrastructure separately, allying themselves when executing a given campaign, a circumstance that allows them to devote most of their resources to increasing the destructive capacity of the threats they develop and to promoting the incorporation of mechanisms that allow them to evade detection effectively and efficiently.
In Spain, some of the cyberattacks involving the third load of Emotet, Trickbot and Ryuk affected the Jerez City Council, which paralysed the organisation's virtual services and meant that procedures had to be carried out in person and on paper, four city councils across País Vasco and even the State Public Employment Service (SEPE), which left the organisation inactive throughout the country. They were also allegedly responsible for the cyber-attacks on Prosegur and Cadena Ser. Since then, Spain has become one of the favourite geographical targets of the groups operating these families.
The impact of cyberattacks between 2019 and 2020 by this unwelcome trio prompted Microsoft and several security firms such as ESET, FS-ISAC, NTT, Symantec and Lumen's Black Lotus Labs to join forces to bring about the takedown of the Trickbot botnet, which took effect in October 2020. Since then, there has been a relative slowdown in campaigns involving these malware families. In fact, on 27th January 2021, Europol proudly claimed to have successfully dismantled the infrastructure of Emotet, which has been considered the world's most dangerous malware, thanks to the coordinated and joint activity of law enforcement and judicial authorities around the world.
However, as we have seen in recent days, Emotet's lethargy has ended, since 15th October saw a reactivation of the distribution campaigns of this malware, after a period of inactivity that has reached ten months since that emphatic operation took place.
Although the triad of Emotet, Trickbot and Ryuk was the most publicised circumstance, the reality is that many of today's ransomware actors, such as Conti, ProLock and DoppelPaymer, depended heavily on Emotet's infrastructure to secure initial access to target systems, which has led to its inevitable return. In fact, some researchers believe that Conti may be the successor to Ryuk, leading to the start of a new escalation of cyberattacks based on a three-pronged operation by Emotet, Trickbot and Conti.
From what has been observed until now, it appears that the actors developing Emotet are using the Trickbot infrastructure to re-activate the cyber threat. Moreover, it has been found that campaigns using Emotet are being distributed from emails that are sent from systems that were compromised in the past, without having reached, for the time being, the mass propagation capacity it had thanks to the spam modules. This is a complete restructuring and remodelling, in which the usual techniques are being used, such as delivering the payload through the mailbox, usually with malicious documents attached, to build up a botnet from scratch, with consequences yet to be determined.
The document included in the email message is typically a Word, Excel or .zip file that is password protected, meaning that opening it leads, as in the past, to the execution of either malicious macros or JavaScript code that deploys the payload, first by downloading a .dll file and secondly by loading it into memory using PowerShell. In addition, Emotet continues to employ techniques that attempt to increase propagation capacity, such as mail messages sent from previously compromised accounts and replying to previous messaging threads that were legitimately sent by the real communication partner, which in this case is impersonated by the actors trying to deploy the payload. This technique is intended to compromise new equipment by abusing the trust placed by the receiver of the message in the sender, who is unaware that it has already been compromised. On the other hand, one of the novel techniques incorporated in this new version of Emotet is the use of self-signed authority certificates that allow the use of the HTTPs protocol, protecting network traffic, as well as having modified the encryption and obfuscation techniques of the code.
To sum up, Emotet is one of the biggest malware cyberthreats in existence today, and one whose full potential has perhaps not yet been considered. As we have seen, Emotet goes back in time to retrieve techniques, tactics and procedures that made it successful in the past, while keeping in mind that it does so to secure a better future. Despite the incorporation of certain new techniques that renew this cyberthreat, the actors operating Emotet malware continue to target their cyberattacks at the weakest element in the whole security chain, the user, using social engineering tactics and techniques that abuse the user's naivety, lack of knowledge and trust. In this sense, there are certain practices that are very common in this type of attackers and that denote a lack of coherence through which it is possible to find out that a certain e-mail has not been sent for a legitimate purpose, such as enabling unnecessary macros in office documents or including encrypted attachments with a password when this is incorporated into the message in plain text. Therefore, it is of utmost importance to implement comprehensive prevention measures, such as security policies that disable the execution of PowerShell on devices that do not require it, blocking the activation of macros and configuring endpoint threat detection and response (EDR) mechanisms that block the download and execution of attachments that cannot be inspected because they have been encrypted. Last but not least, Emotet, like so many other cyberthreats, denotes the importance of investing in raising awareness among employees and users, because, although total cybersecurity is a utopia, the most robust system that can be achieved is one in which individuals know the necessary procedures to navigate safely in cyberspace.
While its infrastructure is being reborn, there are echoes and remnants that show that the Emotet cyberthreat has not been eradicated, but on the contrary, it is constantly evolving, trying to implement a new era of crimeware that is likely to be confronted in the future.
¿Qué os ha parecido? Esperemos que haya sido tan interesante para vosotros, como lo ha sido para nosotros. Dejadnos un comentario y compartidlo en vuestras redes sociales :)

Analista de Ciberinteligencia
Entelgy Innotec Security
Bibliografía
https://elpais.com/politica/2019/10/04/actualidad/1570211574_890574.html
https://es.malwarebytes.com/emotet/
https://fidelissecurity.com/threatgeek/threat-intelligence/emotet-spreader/
https://hacking-etico.com/2019/10/08/nueva-campana-del-malware-emotet-en-espana/
https://securelist.com/the-banking-trojan-emotet-detailed-analysis/69560/
https://us-cert.cisa.gov/ncas/alerts/TA18-201A
https://www.businessinsider.es/emotet-malware-acecha-bandeja-correo-571725
https://www.cisecurity.org/blog/emotet-changes-ttp-and-arrives-in-united-states/
https://www.edsitrend.com/2019/10/08/campanas-emotet-trickbot-ryuk/
https://www.incibe-cert.es/blog/emotet-caracteristicas-y-funcionamiento
https://www.incibe.es/protege-tu-empresa/blog/prevencion-y-desinfeccion-del-malware-emotet
https://www.itdigitalsecurity.es/actualidad/2019/11/prosegur-la-ultima-victima-del-ransomware-ryuk
https://www.securityweek.com/emotet-banking-malware-steals-data-network-sniffing
https://www.welivesecurity.com/la-es/2018/11/12/troyano-emotet-lanza-nueva-masiva-campana-spam/
https://apt.thaicert.or.th/cgi-bin/showcard.cgi?g=Mummy%20Spider%2C%20TA542
https://cepymenews.es/ta542-regresa-emotet-principal-amenaza-volumen-mensajes
https://apt.thaicert.or.th/cgi-bin/showcard.cgi?g=Wizard%20Spider%2C%20Gold%20Blackburn